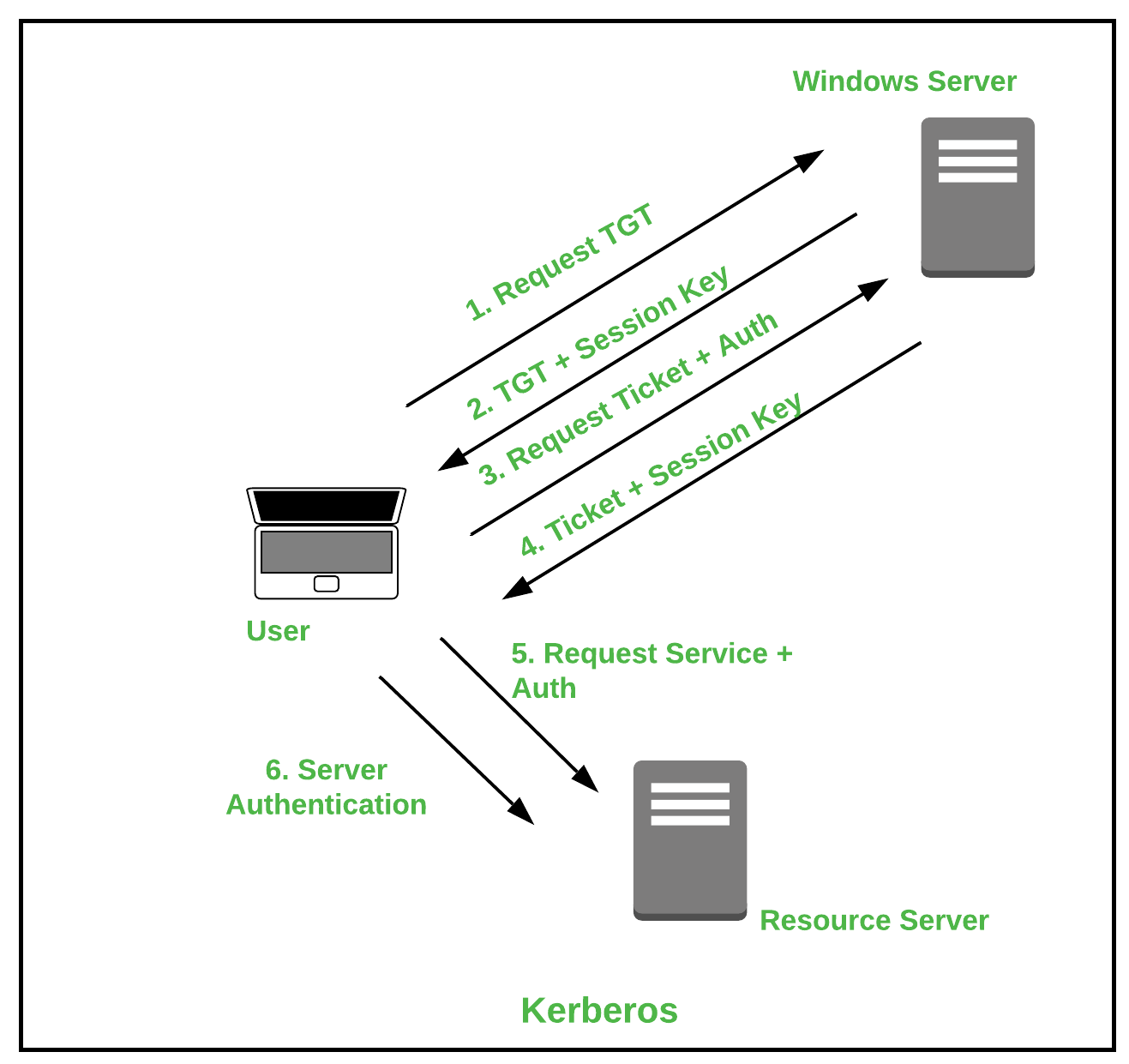
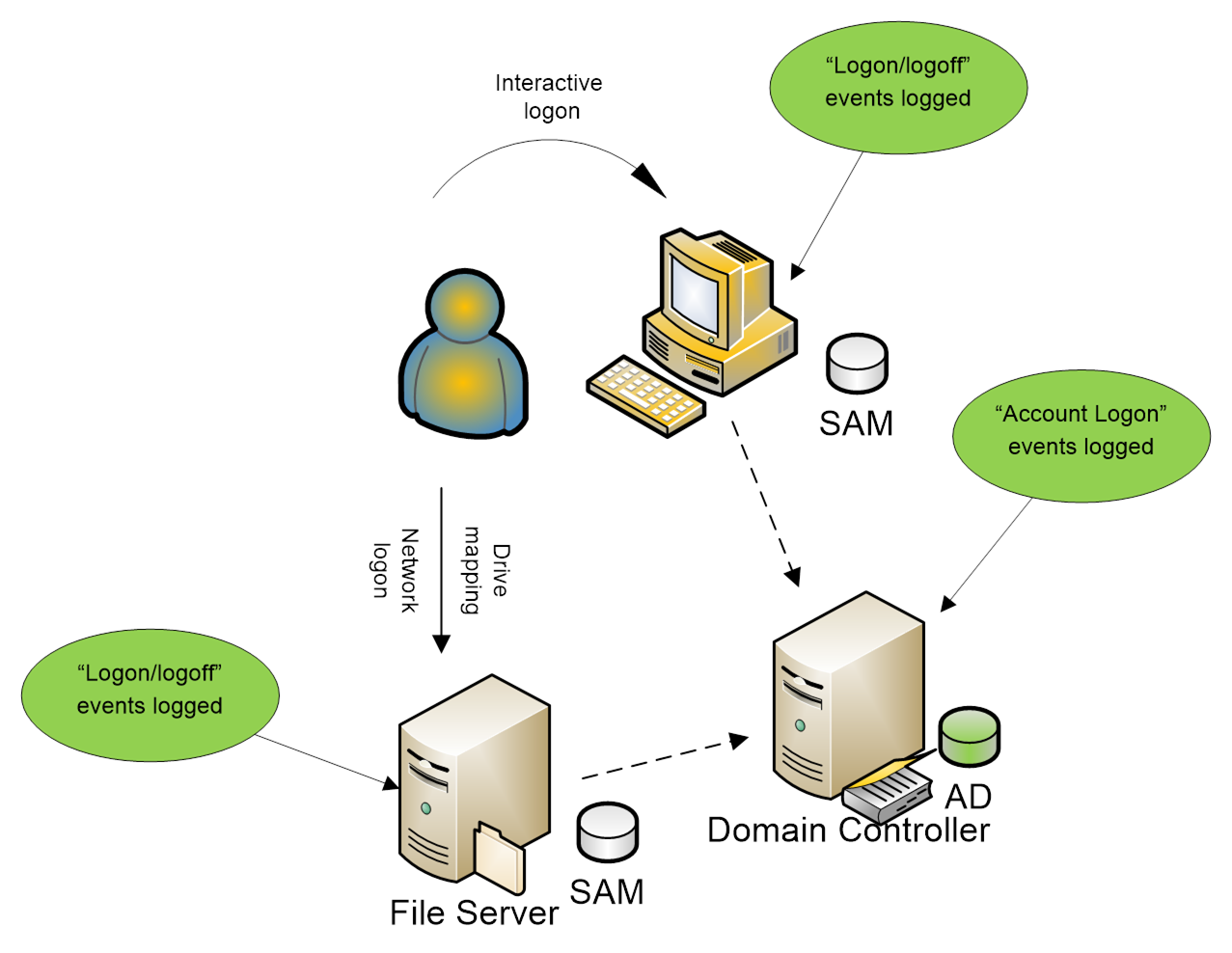
Client Authentication Certificate 101: How to Simplify Access Using PKI Authentication - Hashed Out by The SSL Store™

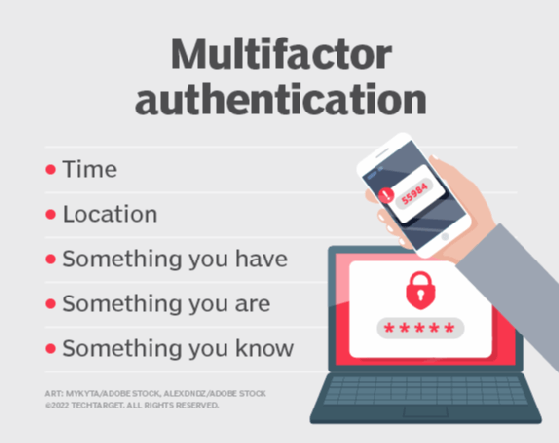
Intro to Your Tech: Authentication - Advantage IT Management Blog | Mobile, AL | Advantage IT Management
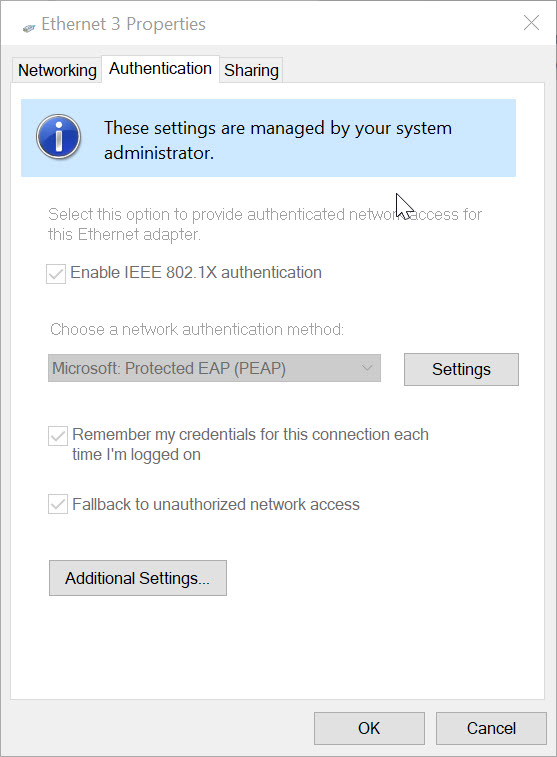
Configuring 802.1x Authentication for Windows Deployment – Part 1 – Building an 802.1x Computer Authentication Script-A Square Dozen | A. Gross Blog