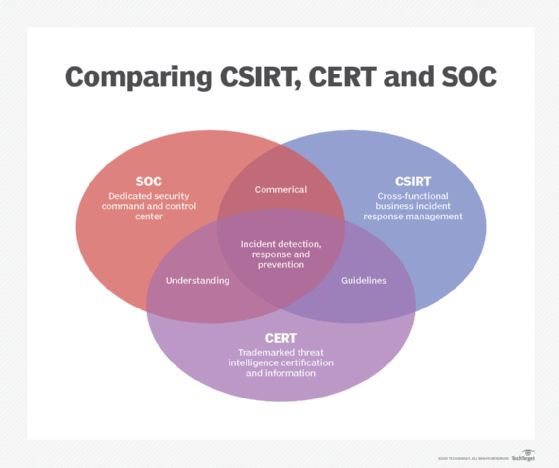
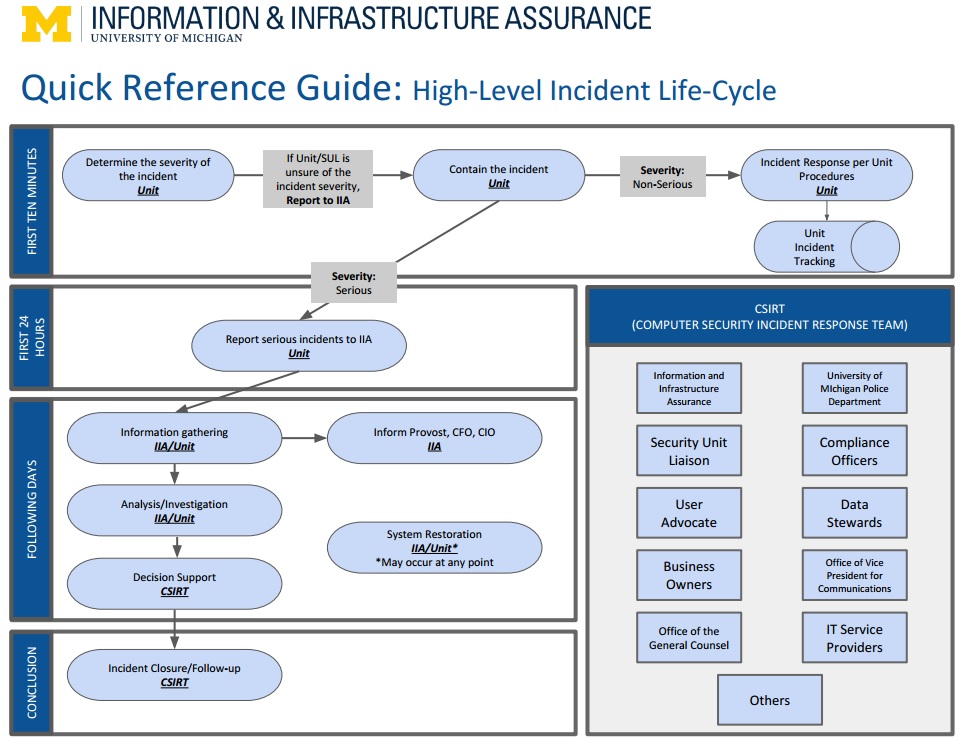
The importance of Cyber Threat Intelligence in Incident Response – Move from Reactive to a Proactive Strategy – IDUNN
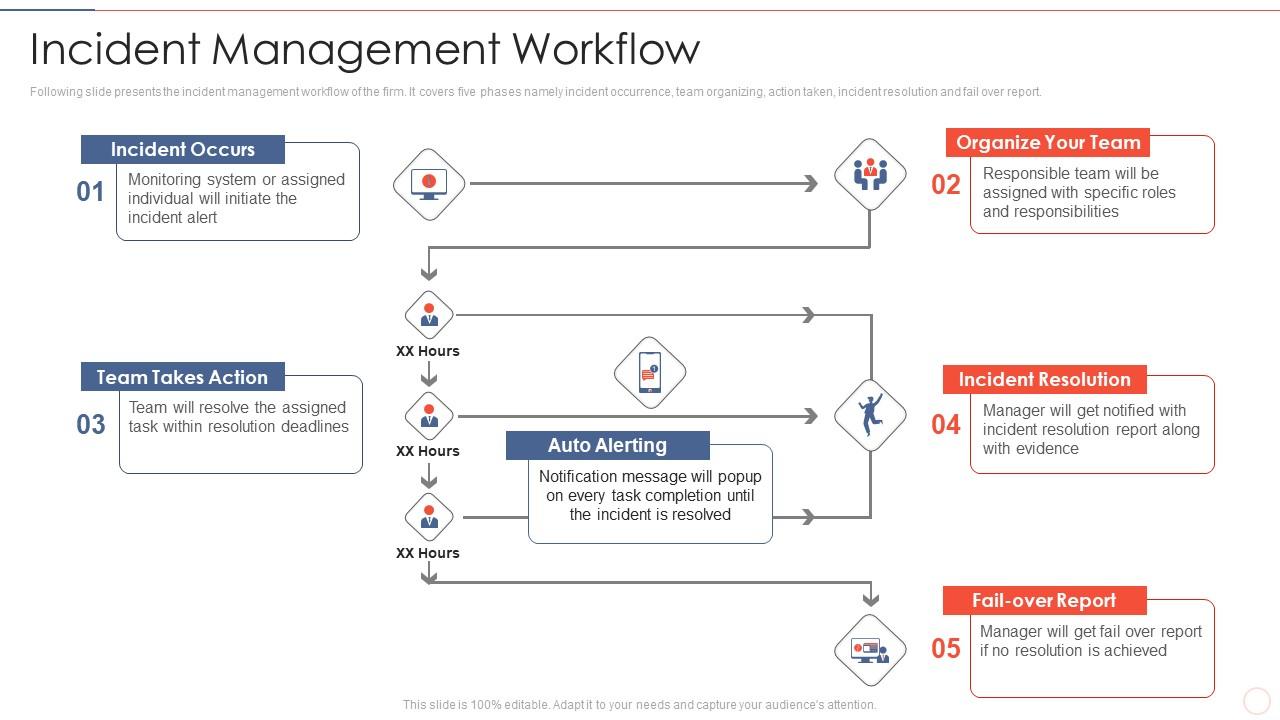
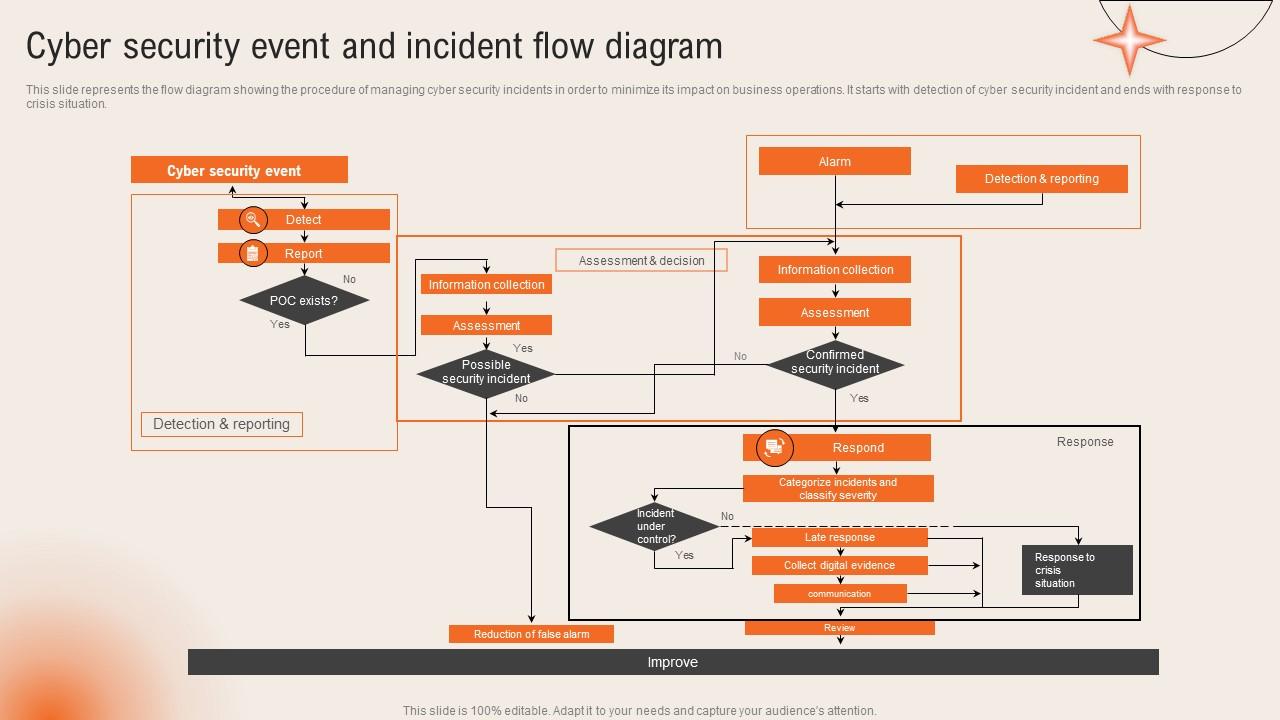
Effective Information Security Incident Management Workflow | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

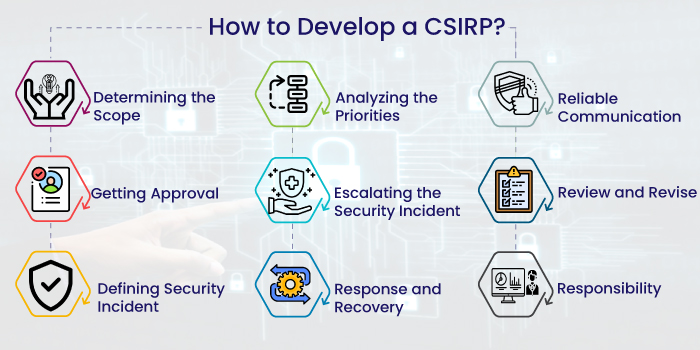
Open platform and tools to facilitate the collaboration among Computer Security Incident Response Teams — ENISA